How To Find Out Who Called Cops On You

OSINT: How to find information on anyone
Your data is more exposed than yous think
Open Source Intelligence (OSINT) — is information gathering from publicly available sources and its analysis to produce an actionable intelligence. The scope of OSINT is not limited to cybersecurity but but corporate, business and military intelligence or other fields where data matters.
Whether you lot are a recruiter, marketing manager, cybersecurity engineer or just a curious person reading the article, you will observe something useful for yourself. Perhaps yous want to know what data of yours is out at that place for others to notice or just want to see if the person or the organization that contacted you online is legit. In this article, I volition explain how to find a person's digital footprint, perform digital investigations, and assemble data for competitive intelligence or penetration testing.
Many OSINT tools are available nowadays so I'm not going to cover them all, merely the most popular ones and those useful in the described apply cases. In this guide, I testify a general approach and different tools and methods that you can utilize depending on the requirements and the initial data you accept. If you lot can't ascertain the starting signal for your investigation — read the article beneath.
OSINT steps
- Kickoff with what you lot know (email, username, etc.)
- Define requirements (what yous want to become)
- Assemble the data
- Analyze nerveless information
- Pin equally-needed using new gathered information
- Validate assumptions
- Generate report
Real proper name

Governmental resources
There are dozens of websites where you tin can find data well-nigh people or organizations and depending on the state, information openness can be unlike. I'm not going to write about information technology in details equally the governmental resource I would provide might not be relevant to you, equally a resident of a dissimilar land. Just remember that such resources exist and Google them in need, every bit they are non that hard to find, especially using the avant-garde search queries I describe below.
Google Dorks
In 2002, Johnny Long began collecting Google search queries that uncovered vulnerable systems or sensitive information disclosures. He labeled them Google Dorks. Since the article is about legally obtained information I'm not going to show how to get an unauthorized access, yet, you tin can explore Google Hacking Database with thousands of different queries. The queries below can return information that is difficult to locate through a simple search.
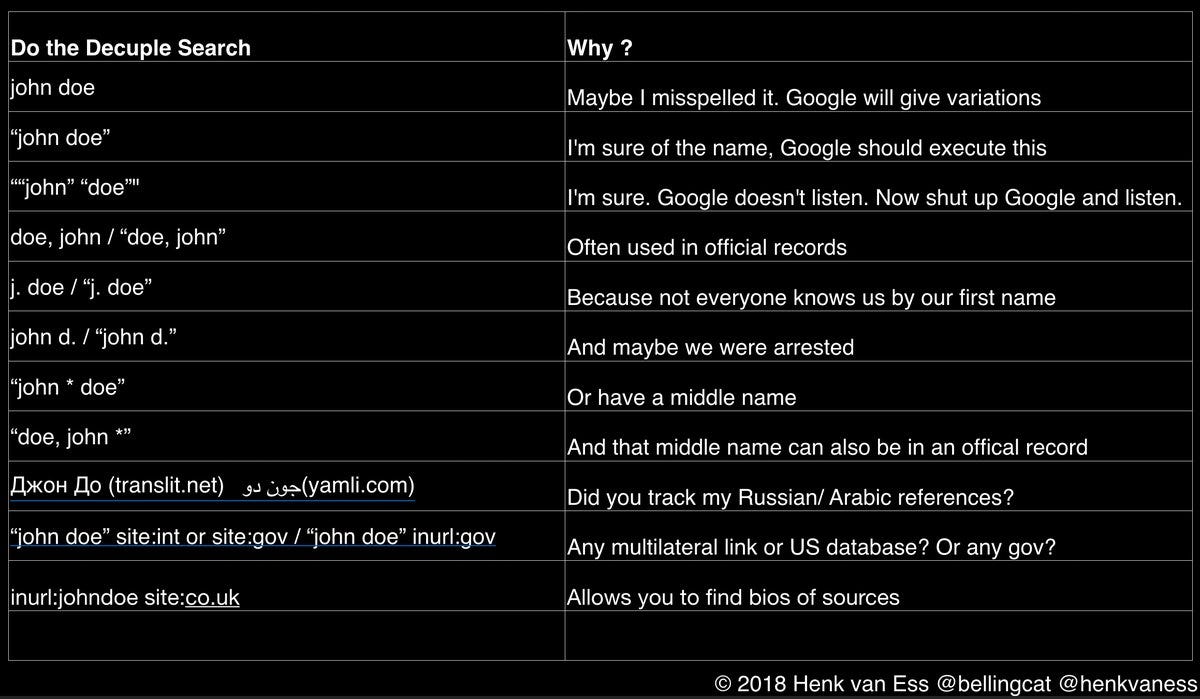
- "john doe" site:instagram.com — quotation marks forcefulness Google Search to do admittedly verbal match while the search is performed on Instagram.
- "john doe" -"site:instagram.com/johndoe" site:instagram.com — hide postings from the target's own account, but show posted comments on the Instagram posts of others.
- "john" "doe" -site:instagram.com — show results that exactly match the given name and surname but in unlike combinations. As well, exclude Instagram from results.
- "CV" OR "Curriculum Vitae" filetype:PDF "john" "doe" — search for the target'due south resumes that contain "CV" or "Curriculum Vitae" in the name and have a PDF extension.
Wrap single words in quotes if you are 100% sure most spelling as by default Google will try to shape your keyword to what the masses want. By the mode, what'southward interesting about Instagram is with the correct Google Dork you can see comments and likes of private accounts.
Perform a search using avant-garde search queries on Bing, Yandex, and DuckDuckGo as other search engines might give you results that Google couldn't.
People search
In that location are websites that specialize in people search which can exist done providing a existent name, username, email or telephone number.
- https://www.spokeo.com
- https://thatsthem.com
- https://www.beenverified.com
- https://www.fastpeoplesearch.com
- https://www.truepeoplesearch.com
- https://www.familytreenow.com
- https://people.yandex.ru
People search websites allow to opt out, but subsequently people remove themselves from listings, new search services appear with their records in them. The reason for that is the same dataset is bought and used by dissimilar services. Some companies own those datasets and even if on one of their websites a person removes the list, on the new domain the old information is repopulated again so the previously removed profile reappears in the search. Consequently, if people did a pretty good at cleaning their stuff up you only accept to wait for a new database to appear. 1 of the methods to discover people that opted out is to go the people search service, find a unique paragraph, do a quoted Google search on it and find all of the domains that the company owns. There are chances that data your target removed from site A is now on site B.
User name
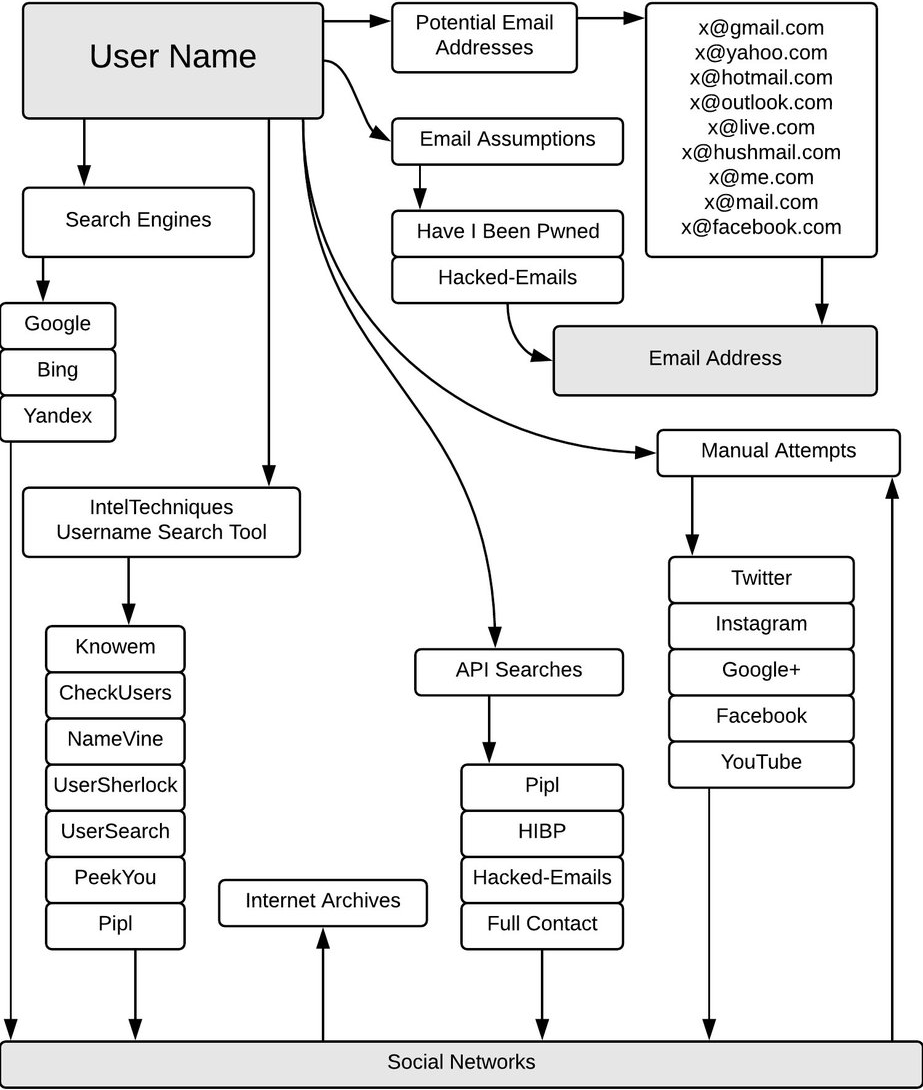
Firstly, we have to find a username. Usually, information technology is a name plus surname combination or derived from the email, domain name of the website the person uses or owns. Outset with data you take and do a reverse lookup towards what you need. Obviously, the simplest way is to Google any relevant data known to you at the moment and endeavour to find whatever pages with the username. Also, yous can utilize special websites that practice a reverse username search, similar socialcatfish.com, usersearch.org, or peekyou.com.
Google Dorks
The aforementioned Google Dorks that I showed for the real name search will be useful when searching for a username. In add-on, URL search might give you good results as unremarkably URLs contain usernames.
- inurl:johndoe site:instagram.com—search for URLs on Instagram that contain "johndoe" in them.
- allinurl:john doe ny site:instagram.com — find pages with "john", "doe", and "ny" words in the Instagram URL. Similar to inurl but supports multiple words.
Depending on the complexity of your search and how successful it was using previous methods you might desire to generate a wordlist. It'south useful when you lot need to endeavor a lot of options as you don't have a clear picture of what username should exist but have a lot of guesses. I have used this Python script for generating the wordlist below:

Username search
In that location are a lot of websites with a username search, I detect these to exist one of the all-time: instantusername.com and namechk.com. Unremarkably, one service finds accounts that other i doesn't and so it's better to employ both websites. Apart from online services you can use WhatsMyName — a Github project, included in more advanced tools: Spiderfoot and Recon-ng. Still, yous tin can utilise it every bit a standalone checker running the Python script.
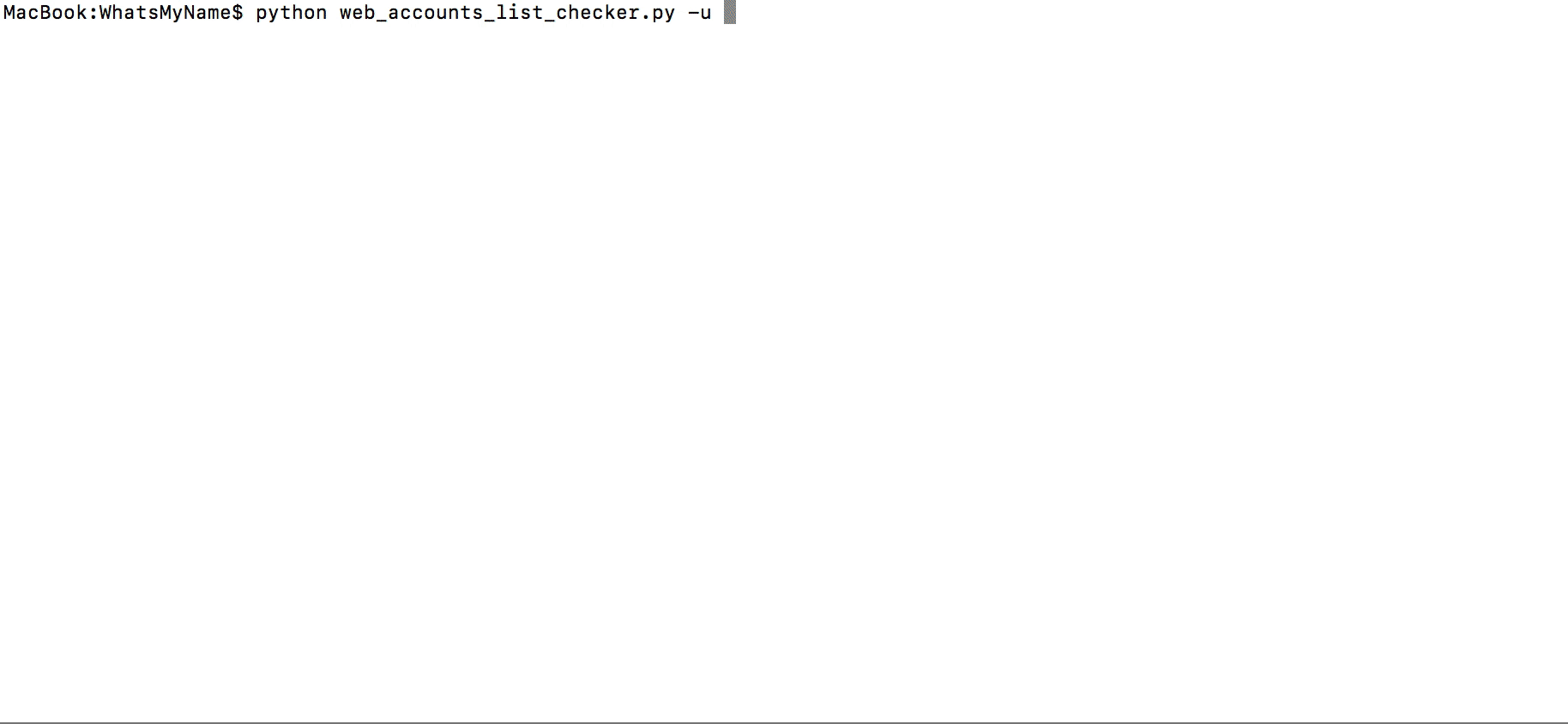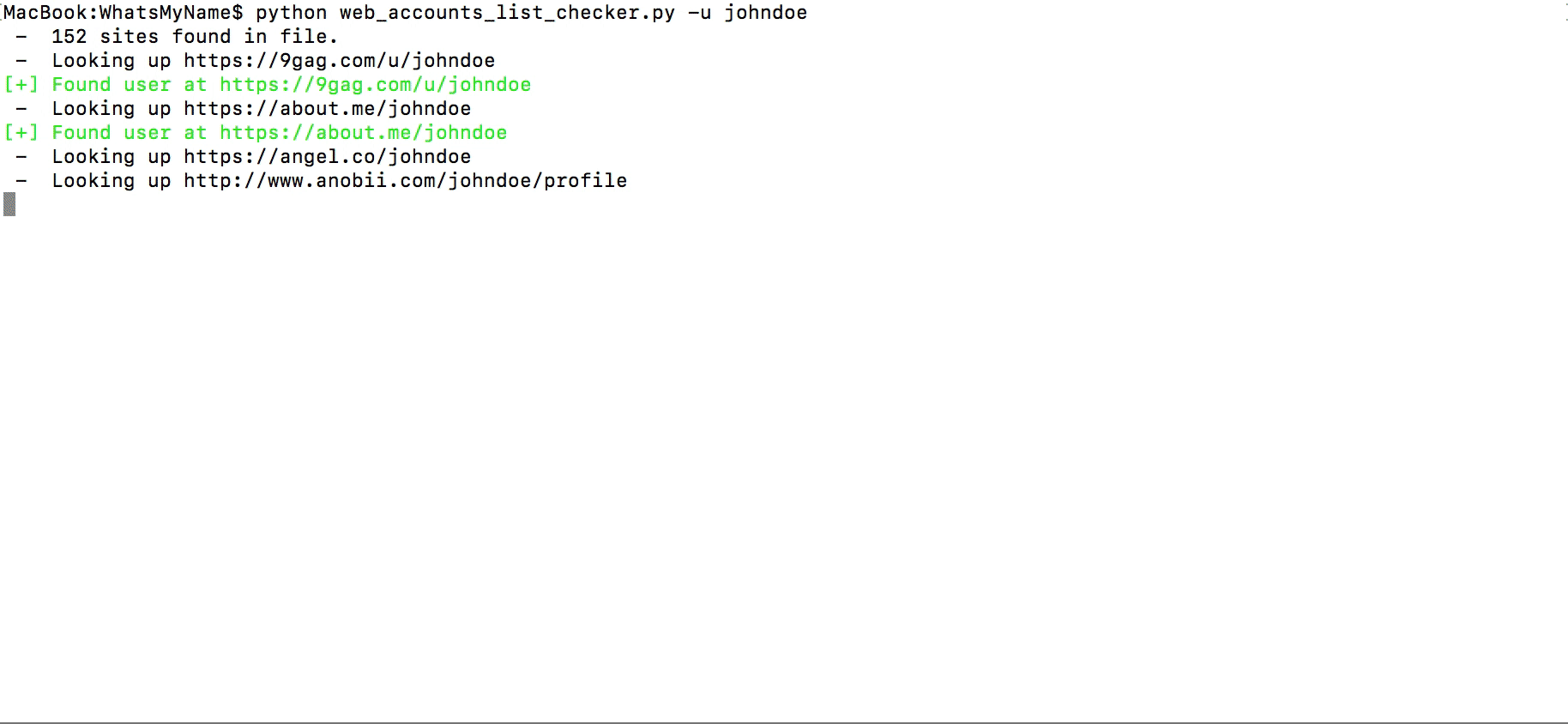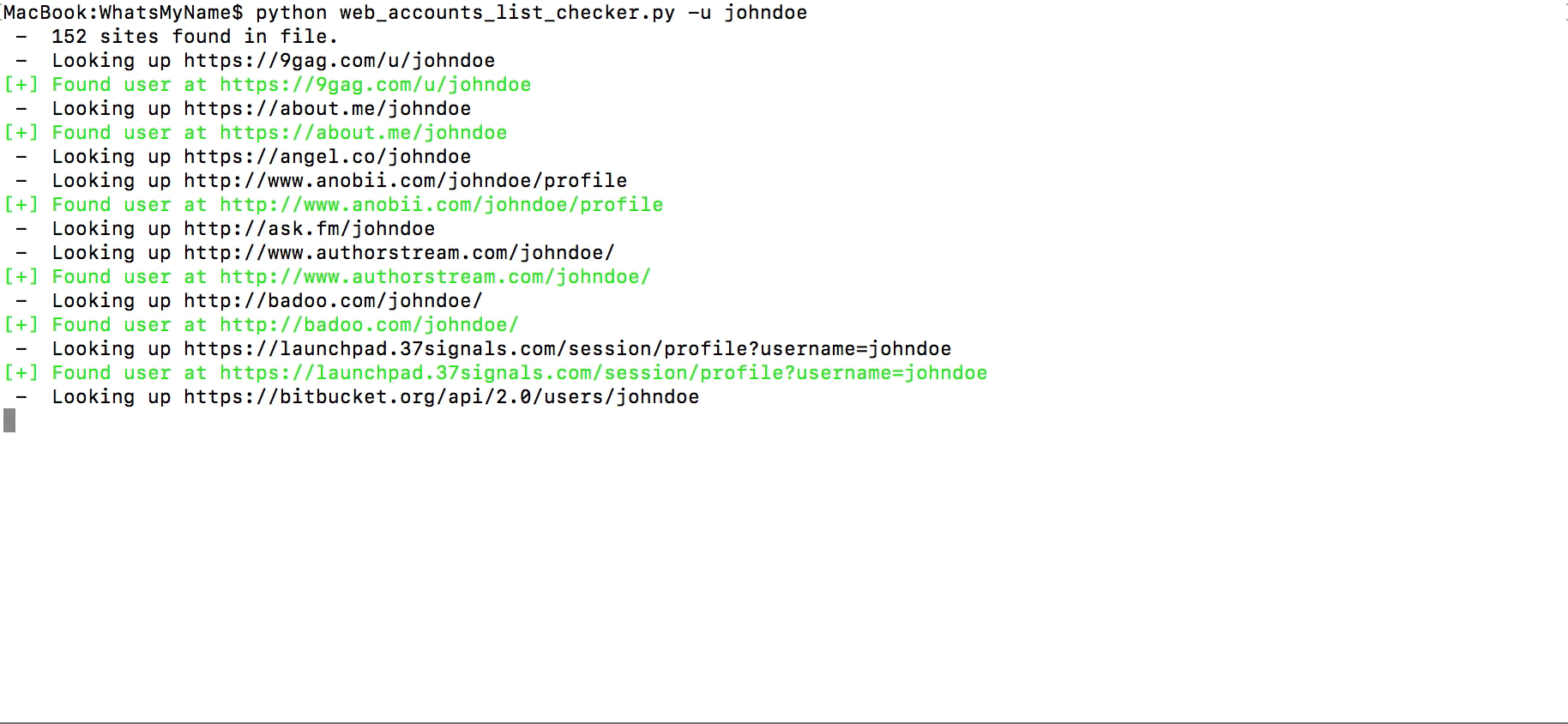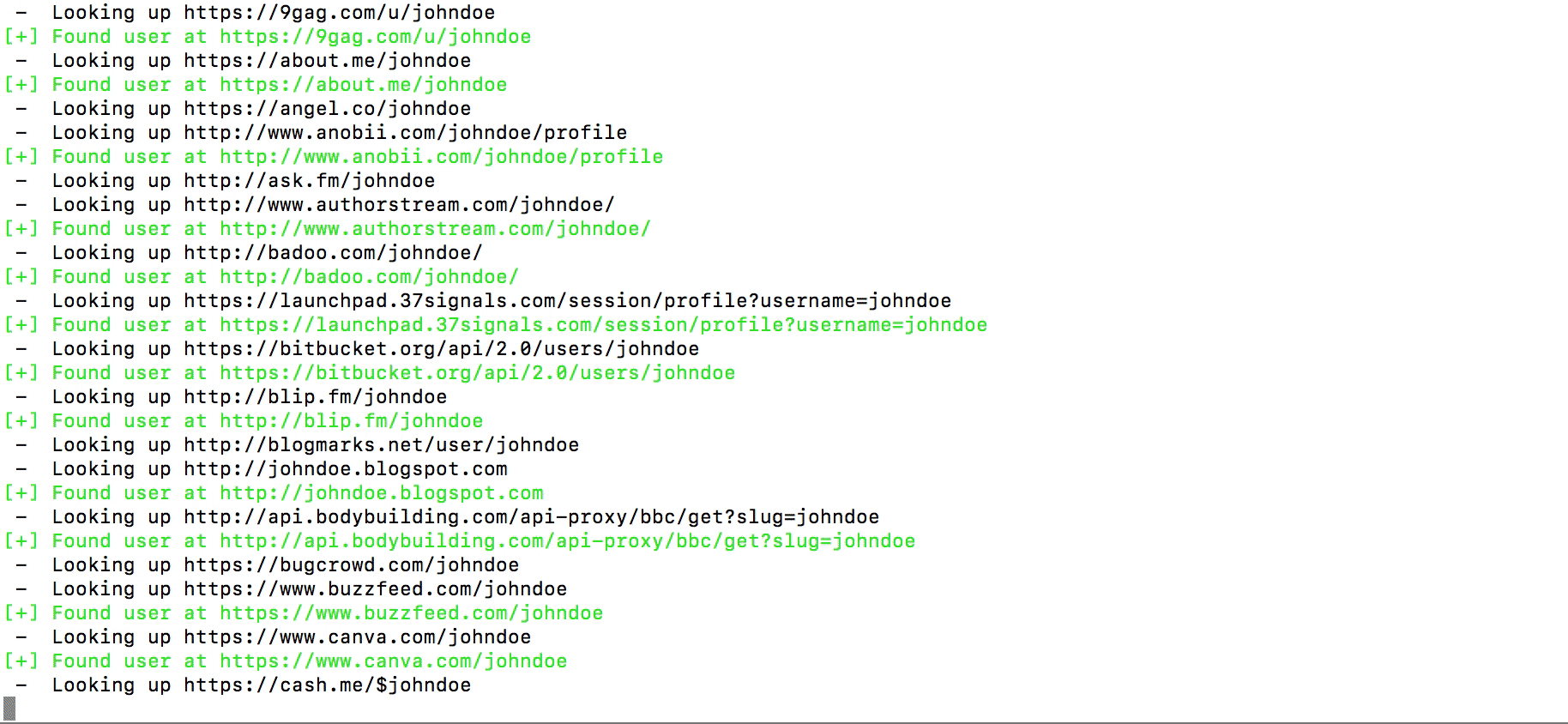
While searching, you lot might get faux positives as someone else can employ the aforementioned username, exist prepared for that.
Note: Running WhatsMyName, too as whatever locally installed tool, could be an issue when y'all have sure websites blocked by the ISP. In that case, going through proxy or VPN will solve the issue. Moreover, to avoid exposure you should use anonymizers anyway.
Email Accost
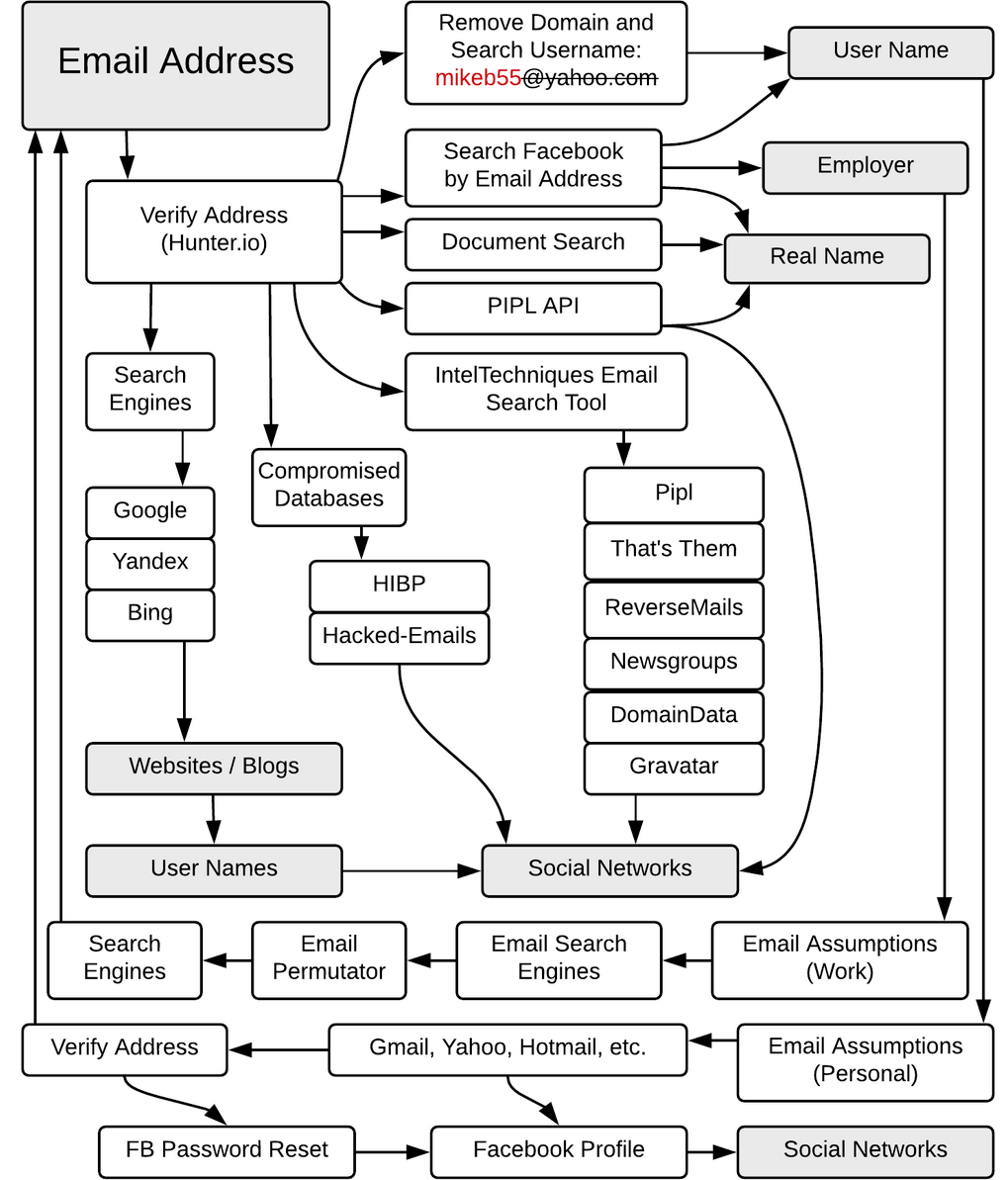
Google Dorks
- "@example.com" site:example.com — search for all emails on a given domain.
- Hour "electronic mail" site:example.com filetype:csv | filetype:xls | filetype:xlsx — detect 60 minutes contact lists on a given domain.
- site:example.com intext:@gmail.com filetype:xls — extract email IDs from Google on a given domain.
Email tools
- Hunter — performs fast scan of the domain name for electronic mail addresses and reveals its mutual pattern.
- Email permutator — generates permutations of upwards to three domains at which target is likely to have an email address. Supports multiple variables input to generate custom results.
- Proofy — allows bulk e-mail validation which is useful when you generated a listing of emails using a permutation tool and want to cheque all of them at one time.
- Verifalia — validates single email addresses for free without registration. To utilise bulk validation you lot have to sign up.
Browser plugins
- Prophet — reveals more data about people. Information technology uses an advanced engine to predict the most likely email combination for a given person based on proper noun, visitor and other social data. Then, Prophet verifies the generated email to brand sure it is right and deliverable.
- OSINT browser extension — contains a lot of useful links, including ones for email search and verification. Compatible with Firefox and Chrome.
- LinkedIn Sales Navigator — plugin for Chrome that shows associated Twitter account and rich LinkedIn profile data straight in Gmail.
Compromised databases
Data breaches take become a big issue and recently nosotros are seeing more and more data dumps. Security researcher Troy Hunt nerveless released data, stripped off passwords, assigned emails to the alienation they were involved in, and uploaded it to haveibeenpwned.com. While the fact of the breach itself might non be equally important, what's of import is with the email you might get a list of services that person uses or at least used.
Another option would exist to utilize dehashed.com. With a gratuitous account it works similarly to Troy Hunt's website merely with an active subscription it shows passwords in clear text or password hashes. From an OSINT perspective, we demand that to search whether it was used on another websites — one more way to find out which services the person uses or at least used. Doing the search by password or its hash shows not just on which website it was used, merely likewise electronic mail address tied to it. Thus, we tin can get the target'due south emails we wouldn't obtain otherwise. It'due south of import to note that if the password is non unique nosotros might get false positives as other people might use information technology as well.
Phone number
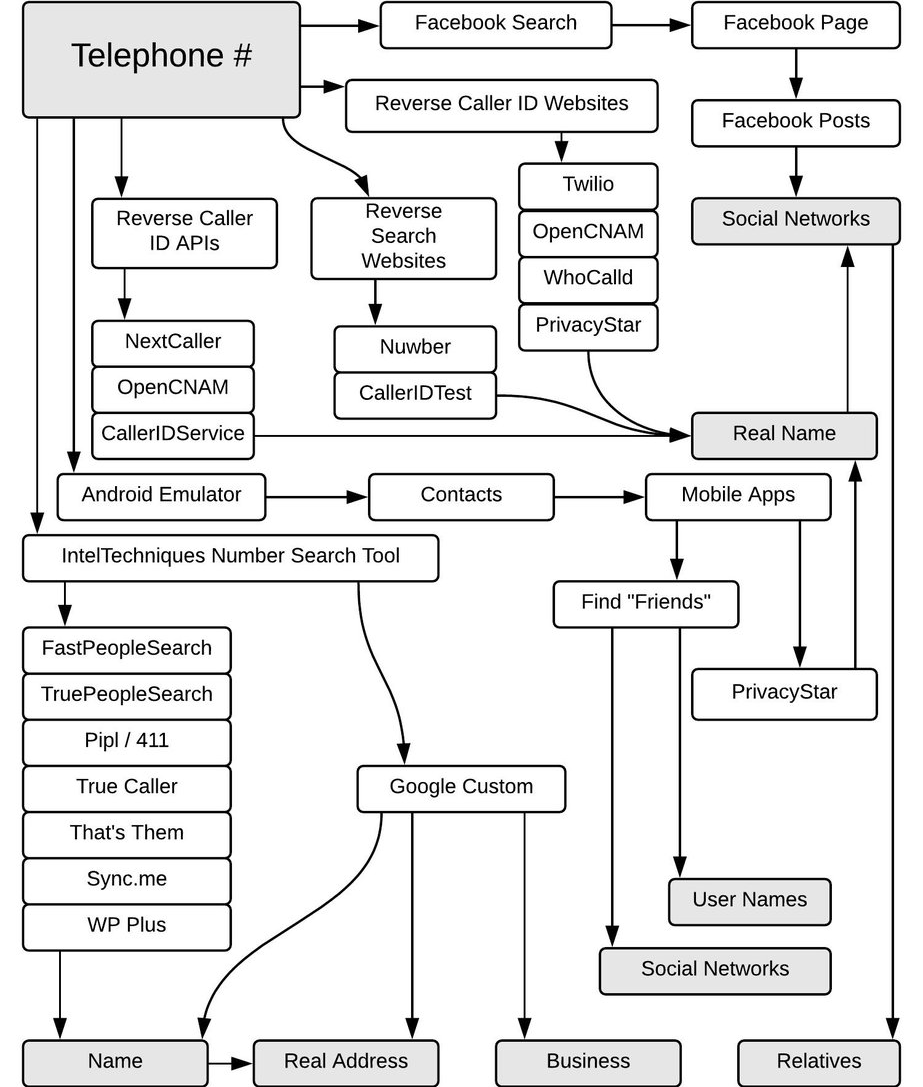
Sometimes people link a phone number and email to their Facebook profile, so typing it in the Facebook search might show you the profile. Some other option is to look upward user-supplied databases of phone numbers, similar whocalledme.com. The database is not express only to America, numbers from Europe can exist checked likewise. Besides, for those who desire something like this but on the mobile device in that location are several apps: privacystar.com, getcontact.com, and everycaller.com. There are many contrary phone lookup services and they are usually country-specific and then discover the one that fits your need.
PhoneInfoga
PhoneInfoga is one of the most advanced tools to scan telephone numbers using merely gratis resources. The goal is to first gather bones information such every bit country, area, carrier, and line type on any international phone numbers with very good accuracy. Then try to determine the VoIP provider or search for footprints on search engines to attempt to place the possessor.
Features:
- Check if phone number exists and is possible
- Get together standard data such as land, line type, and carrier
- Check several numbers at once
- OSINT reconnaissance using external APIs, Google Hacking, phone books, & search engines
- Employ custom formatting for more effective OSINT reconnaissance
Android Emulator
Many Android apps will piece of work on an emulator without issues but some might not work as expected. For case, Viber has problems with VoIP telephone numbers, as tested on freephonenum.com. However, at that place are many advantages running apps on the emulator: your real accounts or telephone number will be safe every bit you don't have to install questionable apps on your phone and you lot can easily spoof GPS coordinates.
Save the number in your telephone and expect at the Viber or WhatsApp contact list. These services allow adding a photograph, biography, and name of the owner and this data tin can exist extracted just past knowing the phone number.
- Bluestacks — made primarily for gamers but runs other apps likewise. Available for Windows, Mac and Linux and doesn't crave a Virtual Car to set it up and so information technology installs easier than Genymotion.
- Genymotion — widely used by developers simply also has a free version for personal utilize. Works on Windows, Mac and Linux and has a range of virtual devices to choose from. Use this guide from IntelTechniques to set up the emulator.
- AMIDuOS — available only for Windows and leverages device drivers from the system to enable near-native functioning in Android. It's fast and has a straightforward installation. However, while the aforementioned emulators tin exist installed for complimentary, AMIDuOS comes at a price of $10.
Domain proper noun
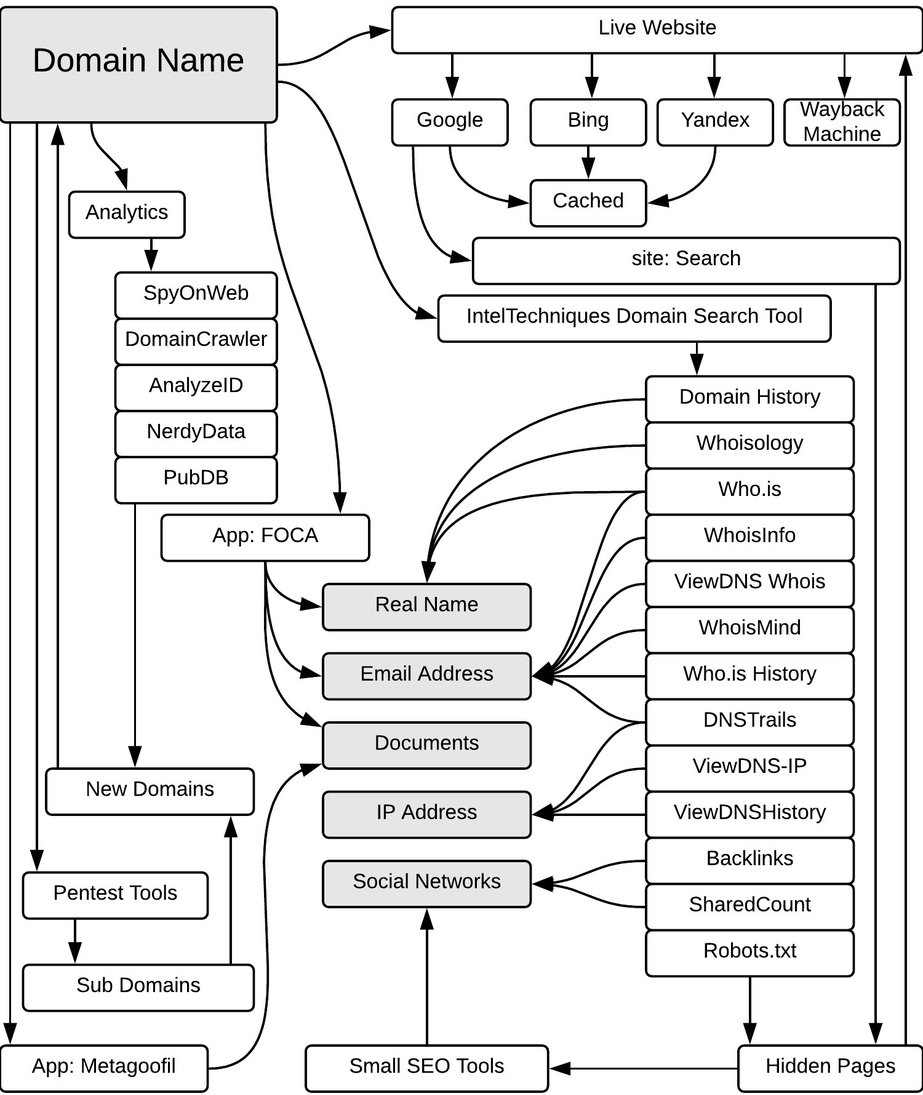
If the person or an organization owns a website y'all should know how to catch information most information technology. The investigation might reveal the operating organisation existence used, software version, personal contact info, and more. I take to mention that it is advised to investigate without always 'touching' the target's environment, such technique is called passive reconnaissance — footprinting that involves the uses of tools and resources that can assist in obtaining more than data nearly your target without straight interacting with information technology. Below I describe methods of obtaining information while remaining hidden.
Google Dorks
Google Dorks is a passive information gathering method that was already mentioned above. Here I'm going to show what queries might be useful during domain investigation.
- site:case.com — limits search to a particular website or domain.
- filetype:Physician — returns DOC files or other specified types, such as PDF, XLS and INI. Multiple file types can exist searched for simultaneously by separating extensions with "|".
- intext:word1 — search for pages & websites that contain the specific word that you are searching.
- allintext: word1 word2 word3 — search for all the given words in a page or website.
- related:example.com — will list web pages that are "similar" to a specified web folio.
- site:*.example.com — show all subdomains. Asterisk acts as a substitute for a whole word or words in search queries.
Whois
Whois provides information about the registered users or assignees of an Internet resource, such equally a domain name, an IP accost block, or an autonomous organisation. There are many Whois resources, these are the good ones: whois.icann.org and whois.com.
Reverse Whois
Reverse Whois gives you a list of domains that have the aforementioned organization name or electronic mail accost in their Whois record. For instance, if you are investigating a company with the name "John Doe Inc." yous can see all the other domains registered under the "John Doe Inc." Ane of my favorite websites is viewdns.info every bit it has an extensive toolkit, including reverse whois lookups.
Same IP
Often discovering what site is running on the aforementioned server as your target'south website uncovers valuable data. For example, you might notice sub-domains or development sites. Often the service provider who hosts this site is responsible for other services as well — use world wide web.atsameip.intercode.ca and www.sameip.org to check information technology.
Passive DNS
Using only DNS records you can encounter what IP resolved to the proper name or what name resolved to the IP. Sometimes that is not enough and that'due south where passive DNS records come up in handy. They allow to check all the names that resolved to the researched IP, thus yous tin build a useful history of resolutions. My favorite product is RiskIQ Community Edition because information technology gives more information than just passive DNS. VirusTotal or SecurityTrails can be used for that purposes besides.
Cyberspace archives and cache
The WaybackMachine tin can be used to find previous versions of webpages, enabling one to see how websites looked earlier or to recover deleted pages. Annal.today is another time capsule for spider web pages with the power to manually add live url snapshots to the archive.
There are cases when deleted pages were not archived but are nevertheless cached by search engines. They can be found on cachedview.com or yous tin can request the cached version with the following Google query: cache:website.com. Didn't find anything on Google? Check the cache of other search engines simply keep in mind that the enshroud shows the terminal time the page was indexed. Therefore, you might become the folio with missing images and outdated information.
You may also similar visualping.io — a monitoring service that takes screenshots of the webpage at the selected time and sends yous an email alert if something changes.
Reputation, malware, and referrals analysis
Reputation is of import to know with whom you are dealing with and whether the website can be trusted. In case of any suspicions, a malicious activity cheque using free online tools might relieve you the trouble of opening the website in the VM or going through other precaution steps. Referral analysis is a search for inward and outward HTML links. Although doing the test on its own is non going to get you precise results, still, it's one of the methods that might show you connected domains.
- www.siteworthtraffic.com — analyses website traffic (users, folio views) and estimates how much revenue it could generate through ads.
- world wide web.alexa.com — analyses website traffic and competitors, shows what they are doing improve and gives advice on SEO comeback.
- world wide web.similarweb.com — analytics tool which provides deep data on website or mobile ranking, operation, the source of traffic, and more. On top of that, it does referral analysis.
- https://sitecheck.sucuri.net — scans websites for known malware, blacklisting condition, website errors, and out-of-date software.
- www.quttera.com — offers free malware scanning and provides a comprehensive report that includes malicious files, suspicious files, blacklisted status, and more than.
- world wide web.urlvoid.com — helps you discover potentially malicious websites. Also, it gives more information about the domain (IP address, DNS records, etc.) and cantankerous-references information technology confronting known blacklists.
IoT search engines
IoT (Net of Things) search engines bear witness yous devices connected to the cyberspace — think Google Search but for Cyberspace-connected devices. Why is that useful? Instead of actively scanning ports and services with Nmap, for example, you can request already available information about open ports, applications, and protocols. Shodan.io is the most popular internet scanner with public API and integration with many security tools. For marketers, it provides data near production users and where they are located. Security researchers use it to uncover vulnerable systems and become access to a broad range of IoT devices. There are other alternatives like Censys, or its Chinese analogies — Fofa and ZoomEye.
Location search
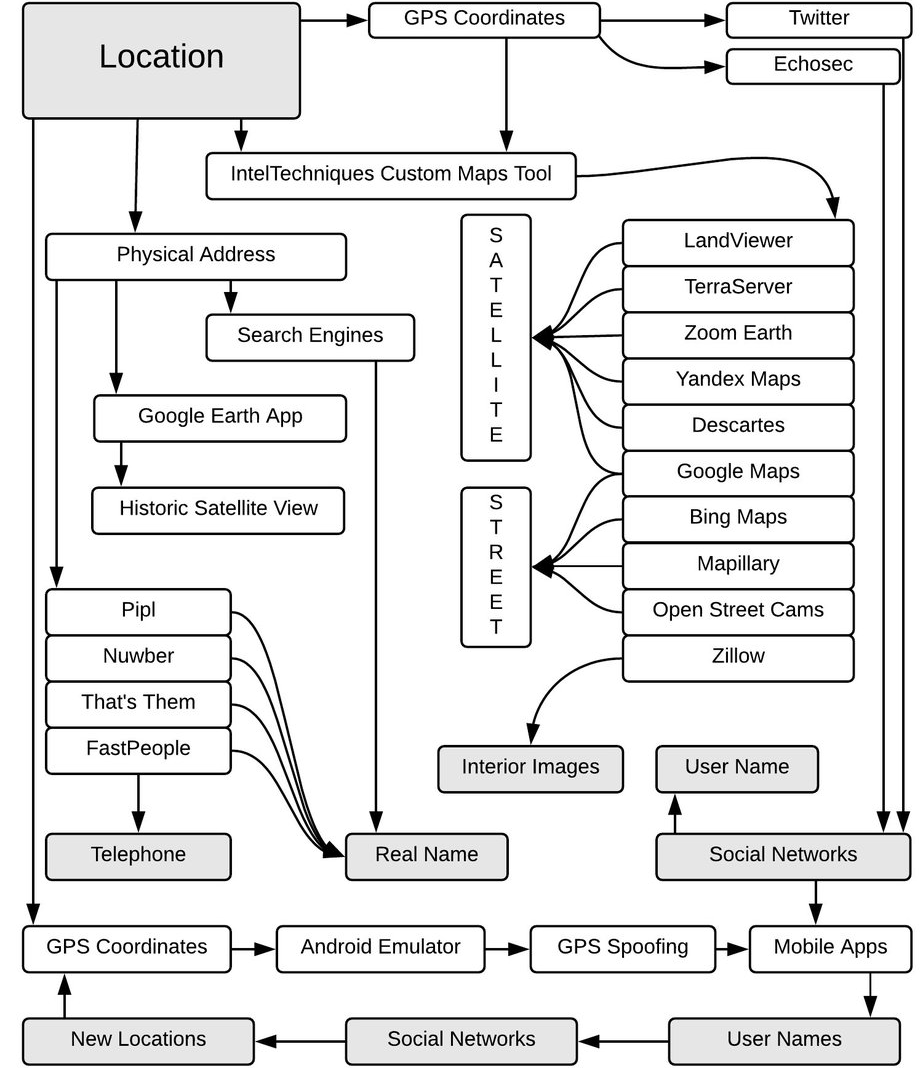
Geolocation tools
Creepy is a gratis tool that allows information gathering from social networks and image hosting services for location research. The commercial option would be Echosec that costs nearly $500 per month.
IP-based Geolocation
IP-based Geolocation is a mapping of the IP accost or MAC accost to the existent-world geographic location. At that place are many websites that map IP accost to location, 1 of them is iplocation.net. When yous know WI-FI access points the person has previously connected to — apply wigle.internet to map them and do more detailed research on Google Globe.
Useful websites
- www.emporis.com — database of compages, provides images of buildings from all over the world. Might exist useful to determine what edifice is on the movie.
- http://snradar.azurewebsites.net — search for geotagged public posts VKontakte and filter them past date.
- http://photo-map.ru — allows to search geotagged VKontakte posts, every bit a previous service, but requires potency.
- world wide web.earthcam.com — the global network of owned and operated live streaming webcams which might be useful during location research.
- www.insecam.org — a directory of online security cameras. The coordinates of the cameras are judge and betoken to the ISP accost and not the physical accost of the camera.
Images
When yous have a picture and want to know where else it is used or when did it first announced — do a contrary image search using Google Images, Bing Images, and Baidu Images. In addition, TinEye's algorithms are designed differently than Google's and as such can render unlike results. Why is that useful? As an investigator, you may find the person by avatar, as people usually don't bother changing profile pictures for the various social networks they use. Equally a announcer, you may perform an image search paired with filtering to expose false news. For example, a picture taken on the twenty-four hour period of the event searched with engagement filter range that is earlier than the described event tin't be found before. Thus, if the image is constitute — it was created before the event, therefore it'due south simulated. If yous need a narrow search across the social network, Findclone and Findmevk.com for Vkontakte or karmadecay for Reddit will do the job. Also, it's worth to mention browser extensions: RevEye for Chrome and Image Search Options for Firefox. Mobile apps like CamFind for iOS might aid y'all searching for things from the concrete world. Moreover, there is an Prototype Identification Project to place what'south on the image using AI.
The image itself contains a lot of useful information, like the photographic camera data, geocordinates, etc. — it'southward called EXIF data and if it wasn't removed yous might find a lot of interesting info. For example, with map geocordinates to find out where the film was taken. With a camera serial number, you can look to see if there are pictures taken with that camera on the internet— stolencamerafinder.com. Image editing tools let to view metadata. If you lot don't want to install a complex program: Exiftool — the cross-platform complimentary software might the thing you are looking for. The third option is to view EXIF data online: exifdata.com or viewexifdata.com. To remove EXIF data you lot can use a locally installed tool: exifpurge.com or do information technology online: verexif.com.
Exercise you demand to perform image forensics and find out if the prototype was tampered with? Use Forensically or FotoForensics. If yous don't desire to upload an image online — Phoenix or Ghiro can be run locally. The latter is more than automatic and gives y'all more functionality than the above mentioned online tools. Apart from that, working with images y'all might need to deblur information technology or improve the quality, then here are some enhancement tools:
- Smartdeblur — restores motion mistiness and removes Gaussian mistiness. Helps to restore focus and do image improvements which deliver amazing results.
- Blurity — focuses merely on deblurring images, doesn't provide such many options like the previous tool and available merely on Mac.
- Letsenhance.io — enhance and upscale images online using AI.
SOCMINT
SOCMINT is a subset of OSINT that concentrates on data gathering and monitoring on social media platforms. I accept already described some social media intelligence techniques. Here I will complete the film past listing more tools.
- ExractFace — extracts data from Facebook, making information technology available offline to utilise as evidence or perform advanced offline analysis.
- Facebook Sleep Stats — estimates sleeping patterns based on users online/offline status.
- lookup-id.com — helps you lot to notice the Facebook ID for a contour or a group.
- Twitter avant-garde search — well, that's pretty self-explanatory :)
- TweetDeck — gives y'all a dashboard that displays separate columns of activity from your Twitter accounts. For example, you might come across separate columns for your home feed, your notifications, your direct messages, and your activity — all in one place on the screen.
- Trendsmap — shows you lot the most popular trends, hashtags, and keywords on Twitter from anywhere effectually the world.
- Foller — gives yous rich insights about whatever public Twitter profile (contour public data, number of tweets and followers, topics, hashtags, mentions).
- Socialbearing — free Twitter analytics & search for tweets, timelines & twitter maps. Finds, filters, and sorts tweets or people by engagement, influence, location, sentiment, and more.
- Sleepingtime — shows the sleeping schedule of Twitter public accounts.
- Tinfoleak — shows devices, operating systems, applications and social networks used by the Twitter user. Also, it shows places and geolocation coordinates to generate a tracking map of locations visited. Maps user tweets in Google Earth and more than.
- www.picodash.com — exports followers statistics of a selected user or statistics by a selected hastag to a spreadsheet (CSV). Also, it exports likers and comments.
- https://web.stagram.com — online Image and Video Viewer/Downloader.
- https://codeofaninja.com/tools/find-instagram-user-id — gets user ID. Usernames might change and then it's useful to know contour's ID to not to lose the page.
- http://instadp.com — shows profile picture in total size.
- https://sometag.org — searches for trending hashtags, locations and accounts. In addition, it compares accounts and exports followers and hashtag statistics.
- InSpy — an enumeration tool that is written in Python. Can exist used to search for employees of a specific system. Additionally, it can find out what technologies the organization uses, which is washed by a crawling job list for specific keywords.
- LinkedInt — scrapes eastward-mail addresses of employees in a selected organization. Supports automatic email prefix detection for a given company domain name.
- ScrapedIn — a Python script that scrapes profile data and imports it into XLSX file (intended to be used with Google Spreadsheets).
Automating OSINT
The Internet is an ocean of data and looking for the information manually might be time-consuming and non effective, plus automated tools could brand correlations you wouldn't spot otherwise. It all depends on your case, whether y'all demand to use these tools or not, as most of them have a steep learning curve and are required to solve complex bug. Thus, if y'all need to accomplish several elementary tasks — don't bother installing software, only utilise online services and standalone scripts I have described earlier. To salve some time and have an investigative environment prepare, with all of these described below tools installed (excerpt FOCA), you lot can download Buscador OS — Linux Virtual Automobile that is pre-configured for OSINT.
SpiderFoot
SpiderFoot is one of the all-time reconnaissance tools out there if you want to automate OSINT as it can be used to query more 100 public data sources simultaneously and its modularity allows to fine-melody queried sources. What I personally liked is scanning by utilise cases. There are four unlike employ cases: get everything and everything about the target, understand what your target exposes to the Internet (done through web itch and search engine use), query blacklists and other sources to check target's maliciousness, and gather intelligence through different open up sources. The terminal 1 is ideal for passive reconnaissance.
theHarvester
theHarvester is a very simple, nonetheless effective tool used to fetch valuable data about the target on data gathering phase. Information technology is great for scanning domain related information and harvesting emails. For passive reconnaissance, theHarvester uses many resources to fetch the data like Bing, Baidu, Yahoo, and Google search engines, and also social networks like LinkedIn, Twitter, and Google Plus. For active reconnaissance, it does DNS reverse lookup, DNS TDL expansion, and DNS brute force.
Recon-ng
Recon-ng is some other dandy command line tool used to perform information gathering thoroughly and quickly. This full-featured Web Reconnaissance framework includes a good selection of modules for passive reconnaissance, convenience functions and interactive help to guide you on how to use it properly. For those familiar with Metasploit, Recon-ng will exist easier to acquire as it has a similar usage model. If you lot are looking for something powerful that can quickly check the visibility of your visitor on the Net — this is the go-to tool.
Maltego
Maltego is an advanced platform developed for analyzing circuitous environments. Apart from data mining, it does information correlation and visually presents it. Maltego works with entities (people, companies, web sites, documents, and more) which you connect for further information gathering about them from dissimilar sources to get meaningful results. The distinctive feature of this tool is "transforms" — a library of plugins that aid to run different kinds of tests and data integrations with external applications.
FOCA
FOCA (Fingerprinting Organizations with Collected Archives) is a tool for extracting hidden data and metadata from analyzed documents. When all documents are analyzed and metadata extracted information technology does automatic metadata analysis to establish which documents were created by the aforementioned user. Also, it does correlation by server and printer. The latest version is bachelor but for Windows.
Metagoofil
Metagoofil is a command line tool that is used to download public documents from websites with the following assay and metadata extraction. It works with pdf, medico, xls, ppt, and other formats.
Conclusion
To conclude, it'due south hard to stay individual in the post-privacy earth and control what data is floating in this digital ocean. While you tin't control everything that's out there about you, it's important to be at least enlightened nigh it. It goes without saying, that in the digital age, information plays a key office, and so those who know how to observe it will always be one pace ahead. That's what this article is for, to show how OSINT helps to solve a broad range of issues: from marketing to investigations to cybersecurity. Nevertheless, I have described merely the tip of the iceberg and nigh techniques in the commodity are simple simply notwithstanding powerful. Therefore, some of the techniques when used in a malicious purpose might cause damage and then utilise them sensibly.
While this article was more about intelligence gathering, the side by side i will be about the preparation phase. Let me know in the comments if there is something specific you want to know about preparing an investigative environs. Past the manner, what tools and techniques do you apply to gather intelligence?
Liked the commodity?
Please, support the hard work and I will write more than often.
BTC: 15XxW1JNDRbzZzKvNyicFFWTefXYte7cPs
ETH: 0x5f88ca7a7dfc671d1e618d1f76d05a0bf85c0d44
Source: https://medium.com/the-first-digit/osint-how-to-find-information-on-anyone-5029a3c7fd56
Posted by: fluddrainglevers.blogspot.com


0 Response to "How To Find Out Who Called Cops On You"
Post a Comment